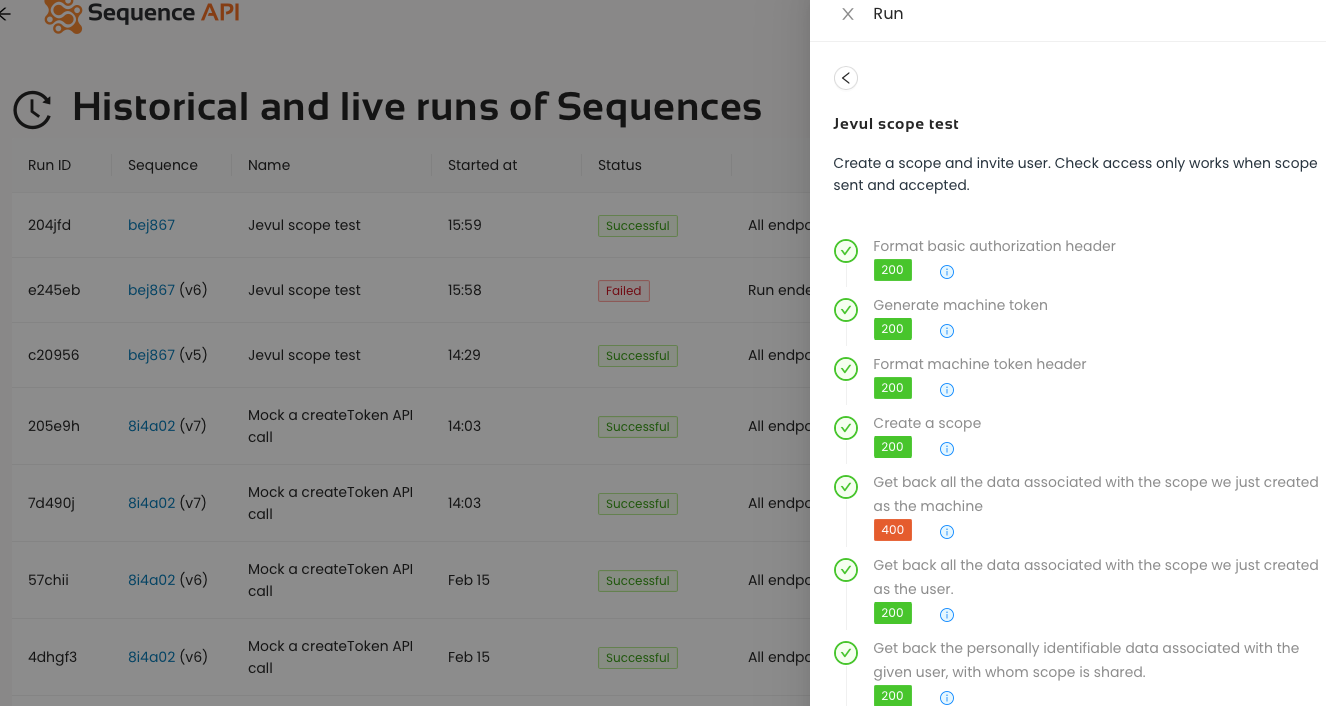
Automating AWS tests dependant on Cognito+API Gateway
We get what it means to build with AWS serverless. Sequence API is built atop AWS. We use a wide range of AWS services including, Lambda, API Gateway, Cognito, DynamoDB, SecretsManager, SNS, Amplify, CDK, Route 53, CloudWatch, CloudFormation, CloudFront etc.
In fact, Sequence API came about because we were developing a privacy product, called Jevul, using Lambda and the same supporting services. We also use Sequence API to build and test Sequence API. Meta! The result is that there are lots of tips and tricks to ease testing services running in AWS which made our lives easier.
Primarily, this means the ease of using your own Cognito service to underpin the security of invocations against API Gateway, where the valid user token needs to be included in the header to the API call.
We are going to use the following example to illustrate this. This is a real test for Jevul and is the source of inspiration for the tutorials on the landing page. It is a complex example but there is no need to understand all the details.
The first thing to note in this example is that it has a lot of inputs. This is partly so that it is easy to apply against different test environments: constantly tear down and build fresh environments on different subdomains using CDK.
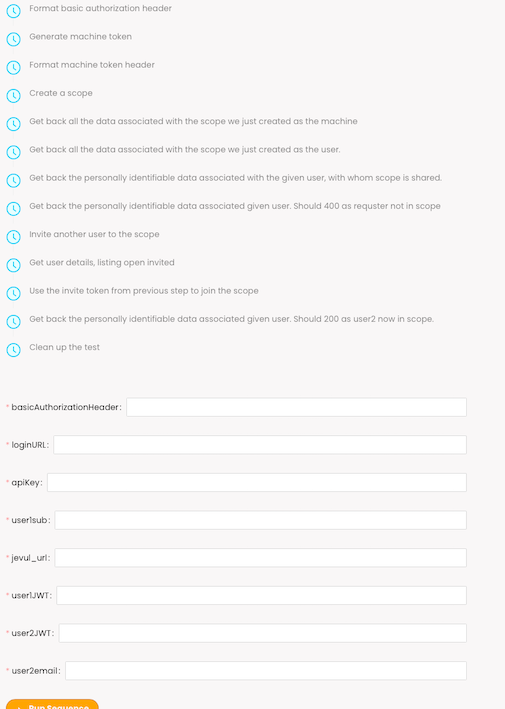
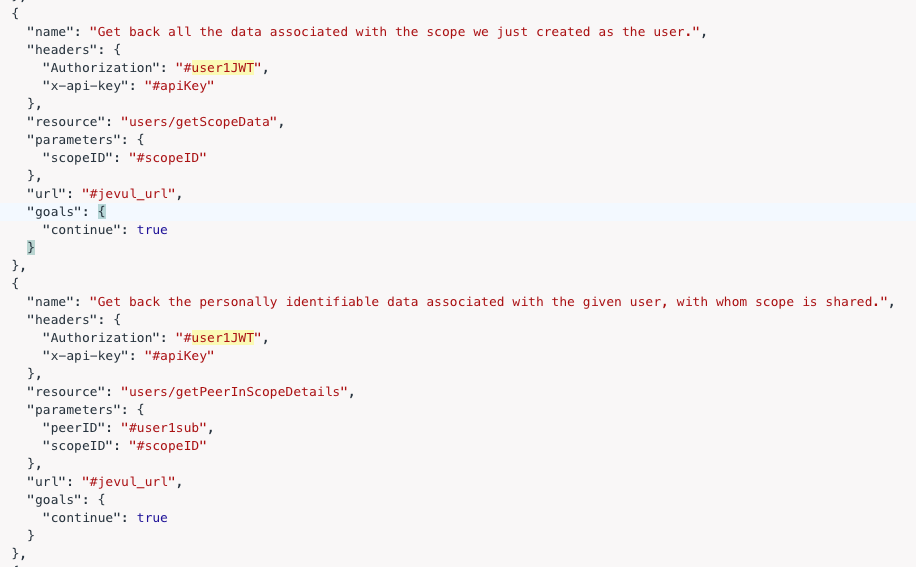
But it is also because we require authentication (cognito) tokens to access some of the serverless functions behind API Gateway, and those tokens should not be in the JSON. We could set the tokens up as secrets but by default tokens expire after one hour. So it is easier to generate those tokens on demand and pass them as inputs to the sequence. We can see the usage of the tokens here (user1JWT):
The following builds on the automation tutorial here. Specifically we are going to use the sequenceapi npm module and write a small nodejs script that runs this sequence.
Sequence API uses a Cognito user pool for authentication. Jevul, the product this sequence tests also uses a Cognito user pool for authentication. The details of the Sequence API user pool are baked into our npm module. Of course, the Jevul user pool details are not and so we are going to provide them.
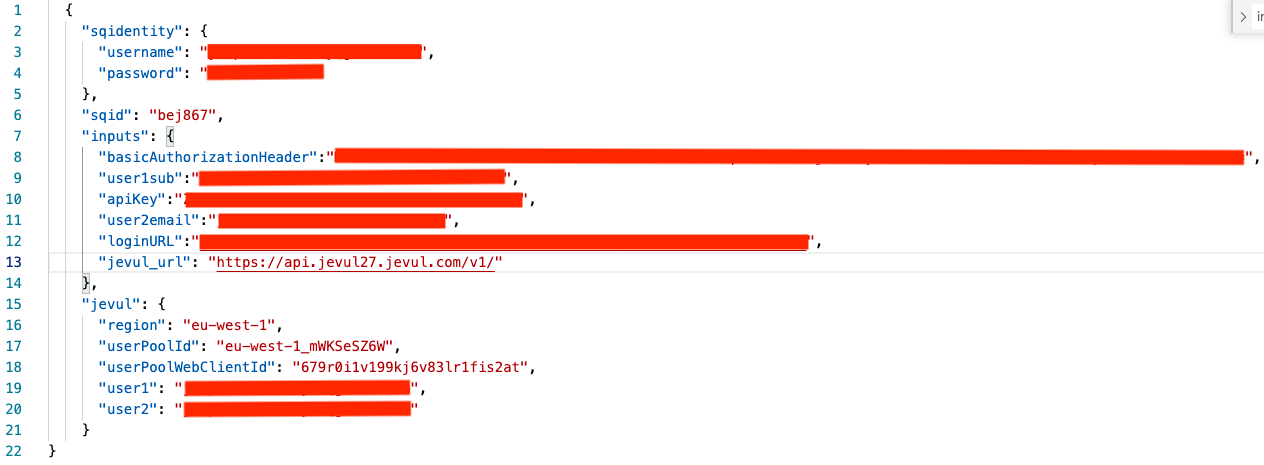
These details are placed in a JSON configuration file. I actually maintain several different versions of this file for my different Jevul environments (dev, beta, prod etc). I have obfuscated account details.
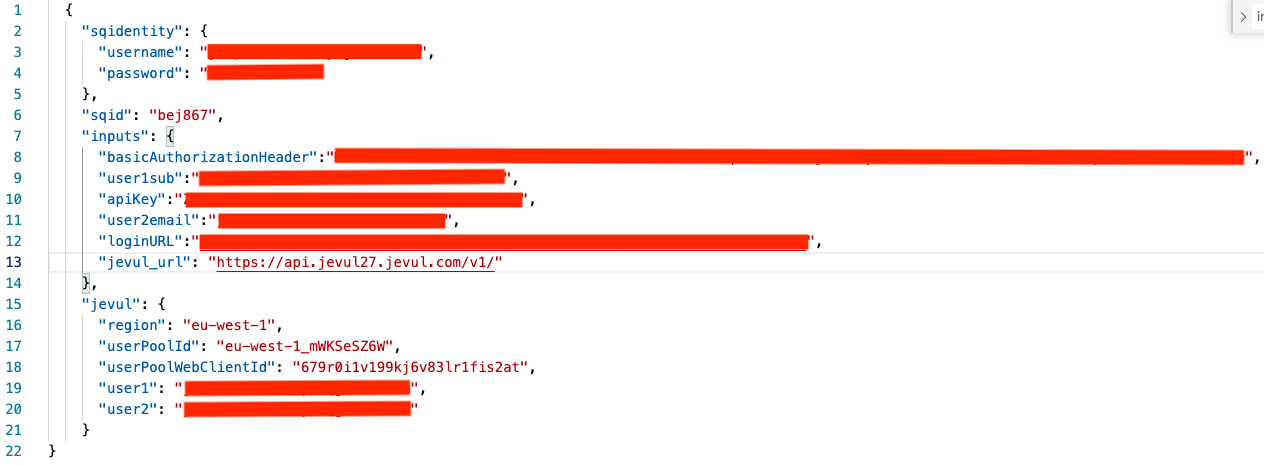
Here is the script that utilises the configuration. The config file is. passed as a parameter to the script when I run it.
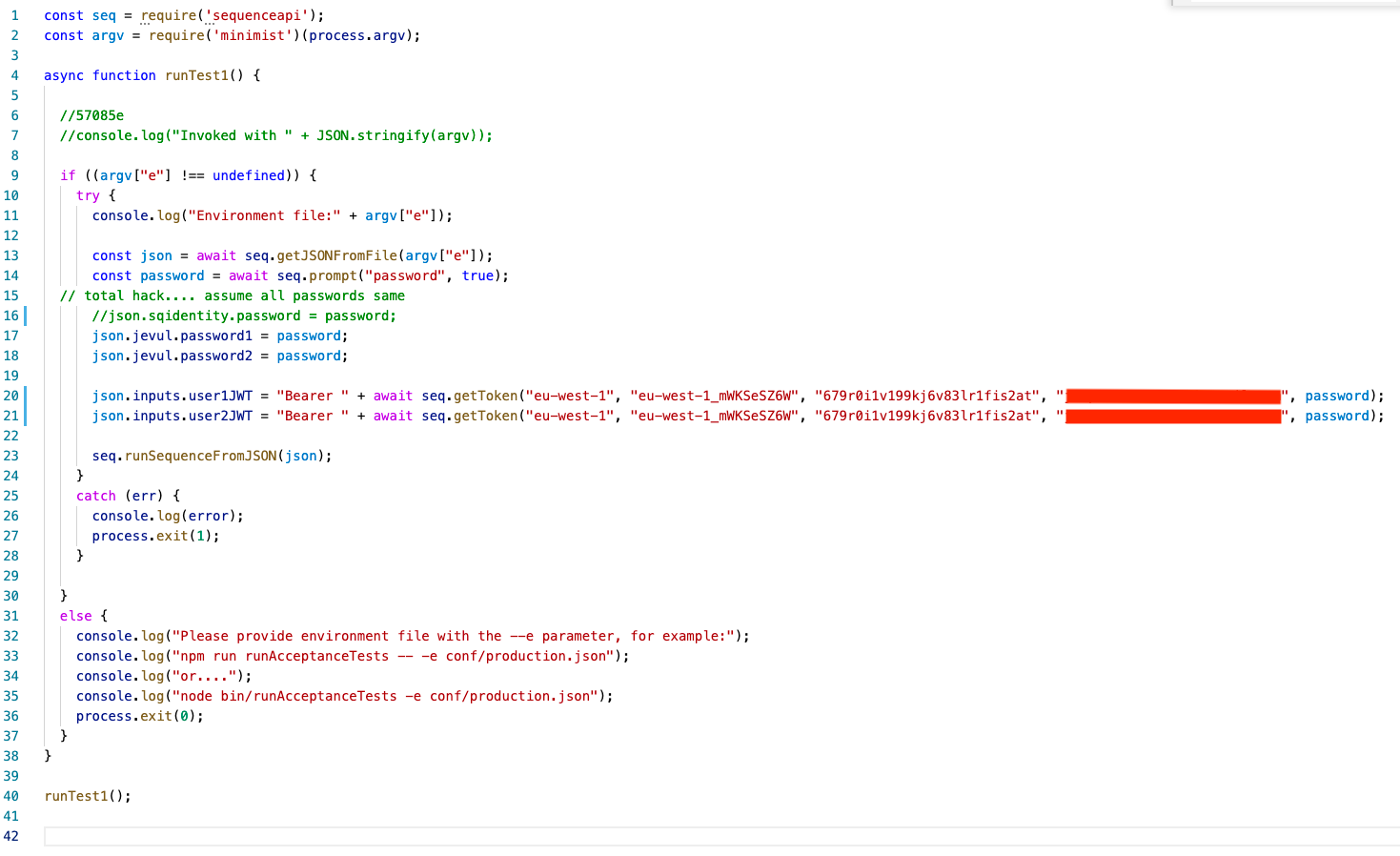
Here are some of the things to note:
- Line 13 uses a facility to load the JSON from the configuration file.
- Line 14 uses a facility to prompt for extra information not included in the configuration.
- Lines 20+21 use a facility to generate valid cognito tokens. This is really Amplify, which is included as an npm dependency to the sequenceapi module. Note that the token is appended to "Bearer ".
- Line 23 runs the sequence.
I then run the sequence from the command line:
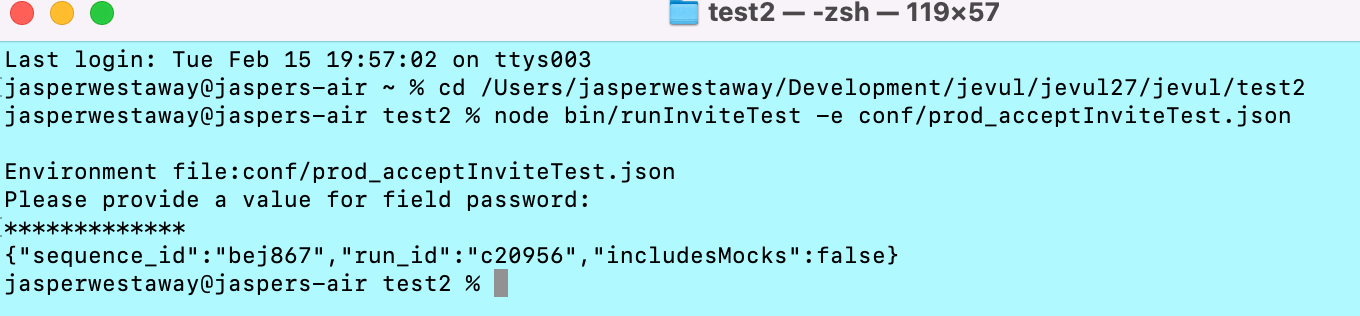
And I can view the results in the browser: